If you need an Anti DDoS service to ensure reliable protection of the server/site, then the company "BitWeb" will help you quickly solve this problem. Here you will be offered the highest level of service at reasonable prices. You will certainly be satisfied with the work of highly qualified programmers.
Protection against attacks of the following classes is guaranteed (but not limited to those listed):
- IP malformedProtection against attacks of the following classes is guaranteed (but not limited to those listed):
- IP Fragment
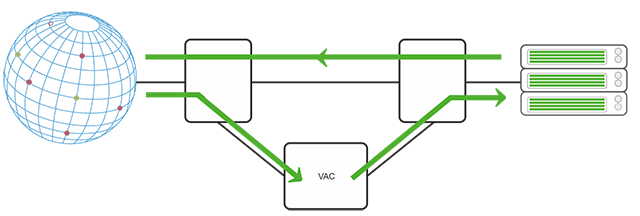
Prevention starts within a few seconds. Incoming server traffic is cleared using our VAC solution. The VAC hardware has a total bandwidth of 4 TBps. The attack is then blocked without any restrictions on volume or duration, regardless of what technique it uses. Legitimate traffic is not blocked and reaches the server. This process is also called automatic prevention and is fully managed by OVH.
Cleaning is one of the main features that makes OVH an outstanding solution for preventing DDoS attacks. DDoS attack channel diversity requires high bandwidth. With a bandwidth of 15 TBit/s, during DDoS attacks, the OVH infrastructure is able to absorb a very large amount of traffic. Another feature of the OVH VAC is that it is repeated in 10 data centers on three continents. VAC is activated simultaneously in all these data centers, so all regions can pool their capacity and absorb traffic. They have a total capacity of more than 4 TBit/s.
| The name of the attack | OSI | attack | The principle of attack |
|---|---|---|---|
| Flood of ICMP messages (echo requests) | L3 | Resource | The so-called ping flood is a mass sending of packets that entails a response from the attacked server with the same content as in the original packet. |
| IP packet fragment attack | L3 | Resource | Sending IP packets with a link to other packets that will never be sent, which overflows the memory of the attacked server. |
| SMURF attack | L3 | Bandwidth | An ICMP bandwidth attack with source address capture to redirect a large number of responses to the attacked server. |
| IGMP flood | L3 | Resource | Bulk sending of IGMP packets (multicast control protocol). |
| Ping of Death | L3 | Exploit | Sending ICMP packets that exploit defects in the implementation of certain operating systems. |
| TCP SYN flood | L4 | Resource | Bulk sending of TCP connection requests. |
| TCP flood with fake SYN | L4 | Resource | Bulk sending of TCP connection requests to capture the source address. |
| Flood TCP SYN ACK | L4 | Bandwidth | Bulk sending of TCP connection requests to a large number of computers to capture the source address of the attacked server. The bandwidth of the attacked server will be filled with responses to these requests. |
| TCP ACK flood | L4 | Resource | Bulk sending of delivery notifications over TCP. |
| TCP fragment attack | L4 | Resource | Sending fragments of the TCP protocol with a link to other packets that will never be sent, which overflows the memory of the attacked server. |
| UDP flood | L4 | Bandwidth | Bulk sending of UDP packets (does not require a previously established connection). |
| Flood with UDP fragments | L4 | Resource | Sending UDP datagrams with a link to other packets that will never be sent, which overflows the memory of the attacked server. |
| DNS attack with avalanche multiplication of data | L7 | Bandwidth | Bulk sending of DNS queries to a large number of legitimate servers to capture the source address of the attacked server. Since the response has a larger amount of data, an avalanche attack occurs. |
| DNS flood | L7 | Resource | Attacking the DNS server with a large number of requests. |
| Flood HTTP (S) GET/POST | L7 | Resource | Attacking a web server with large amounts of requests. |
| DDoS DNS | L7 | Resource | Attacking a DNS server with a large number of requests from a large number of computers under the attacker's control. |